Automate your work at scale with AI agents
Offload lead qualification, deal reviews, CRM data entry, contract review, and other manual tasks to agents.
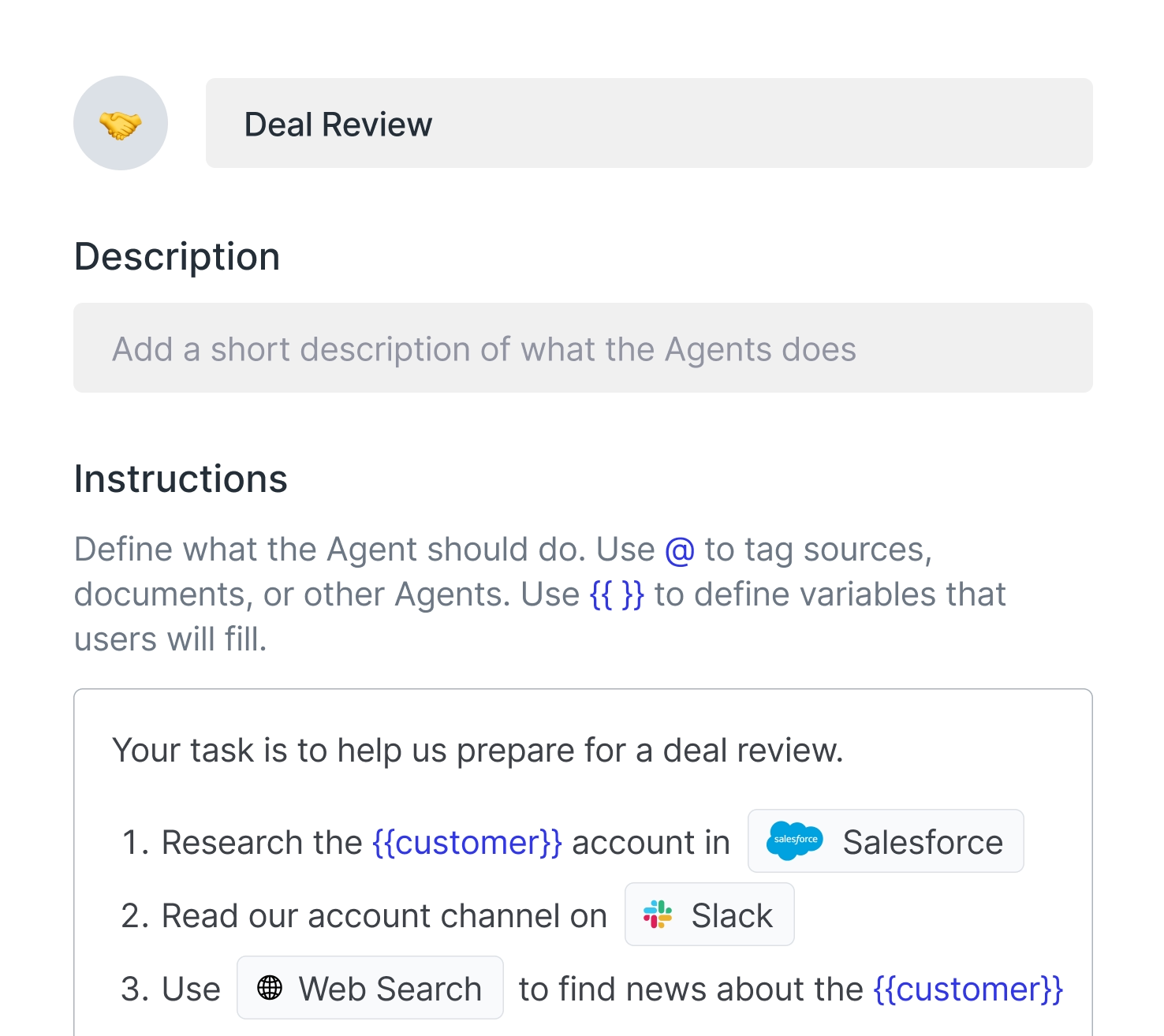
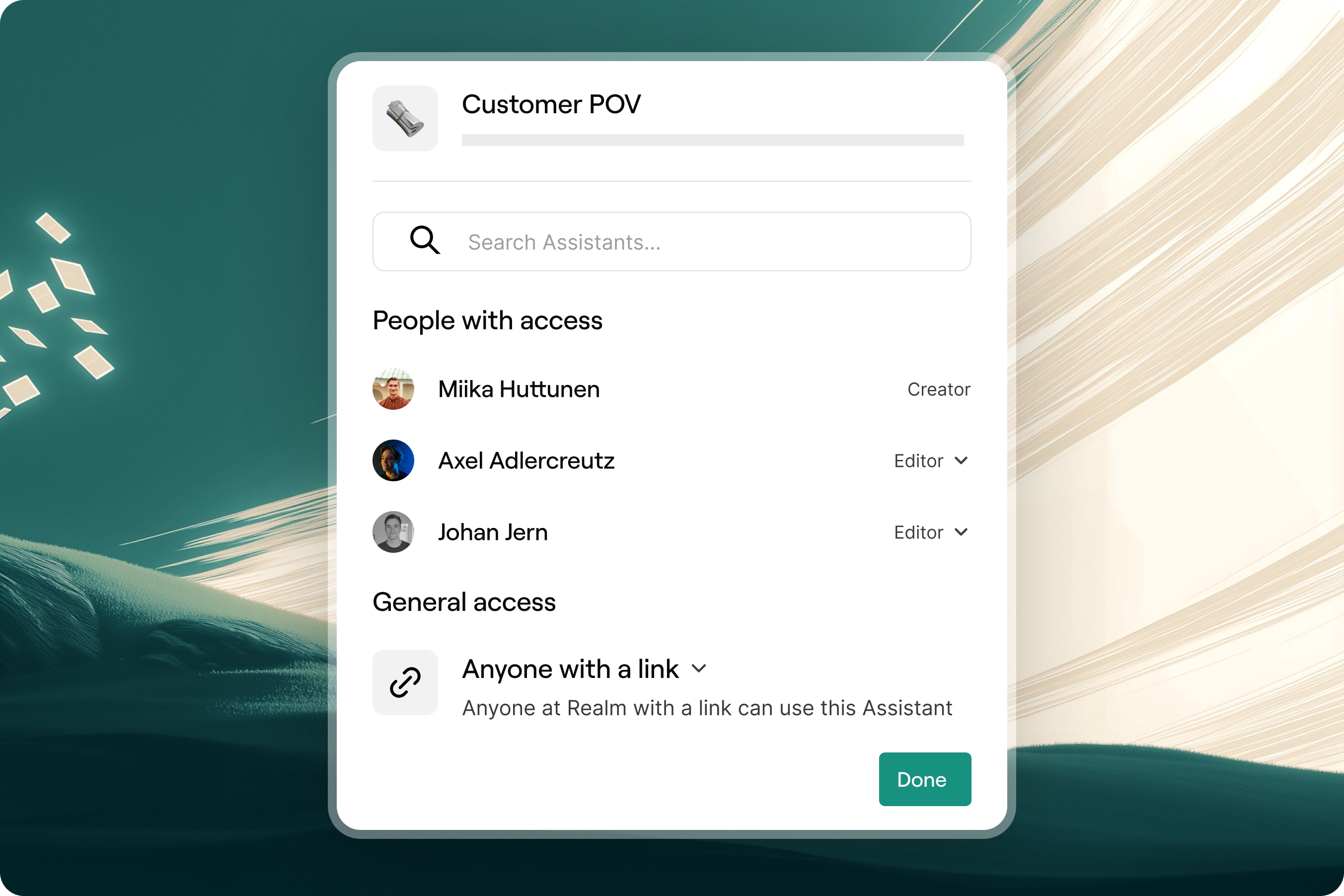
Custom agents for your workflows
Create AI agents without writing a single line of code. Write instructions, define capabilities, and train on your knowledge.
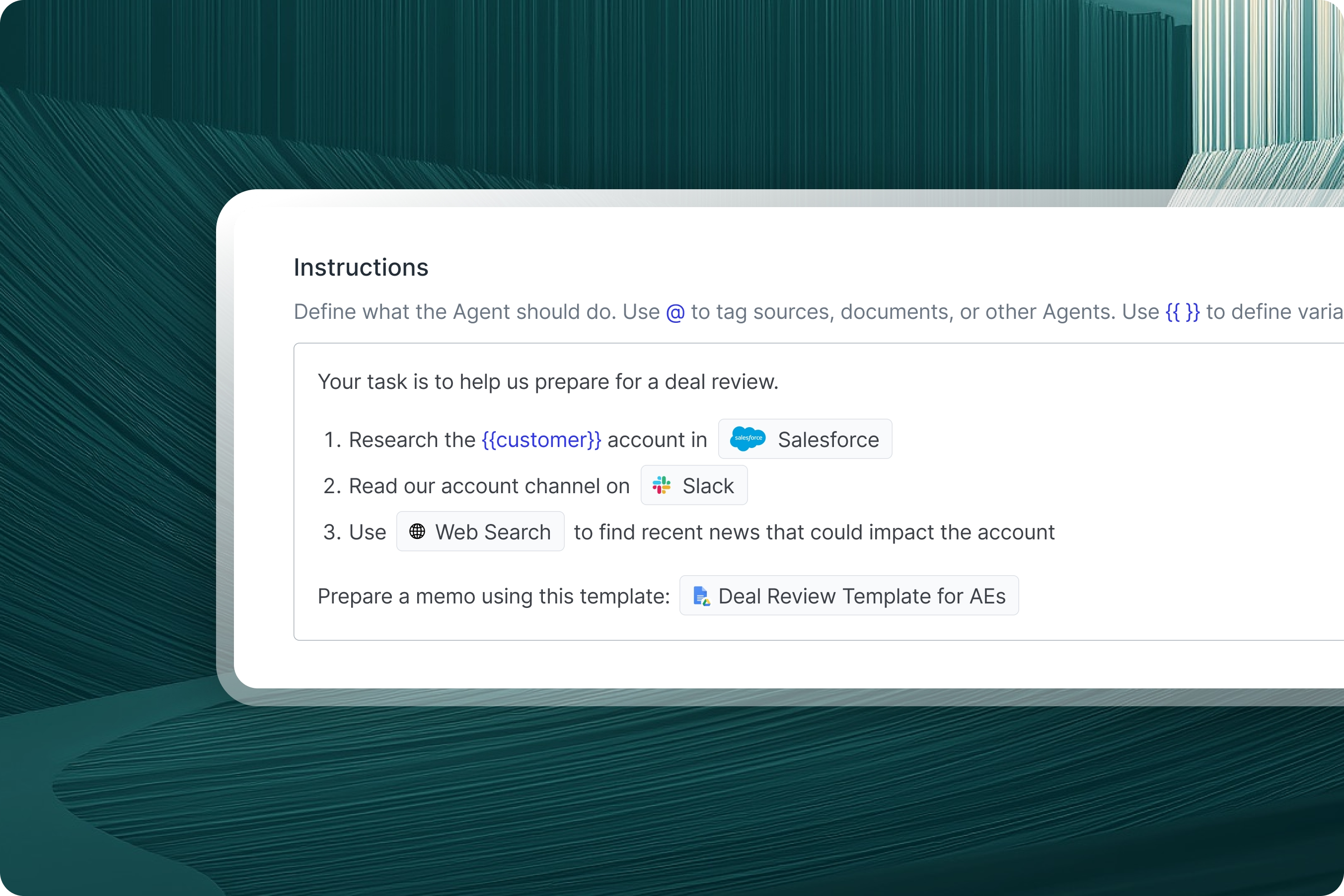
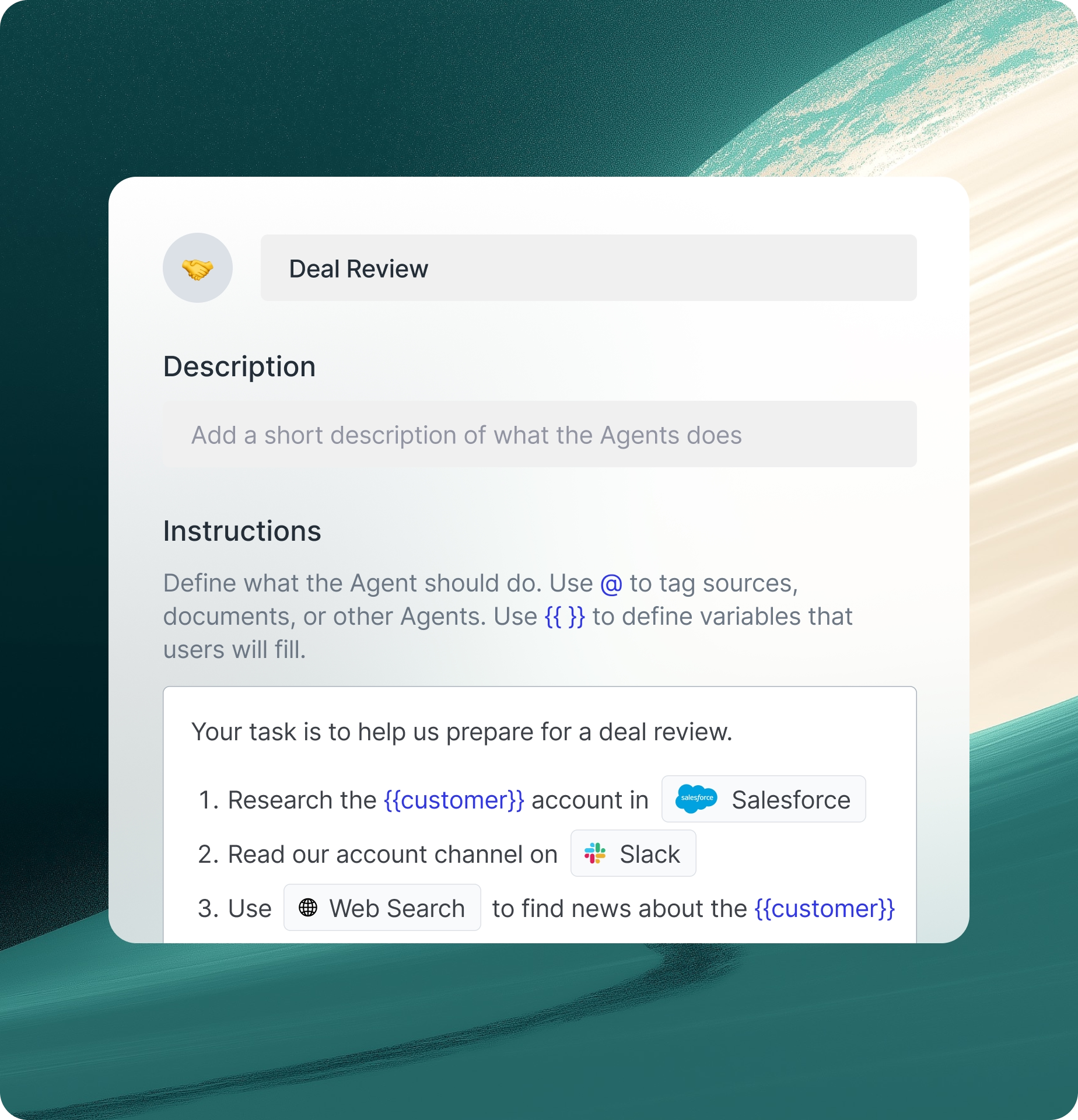
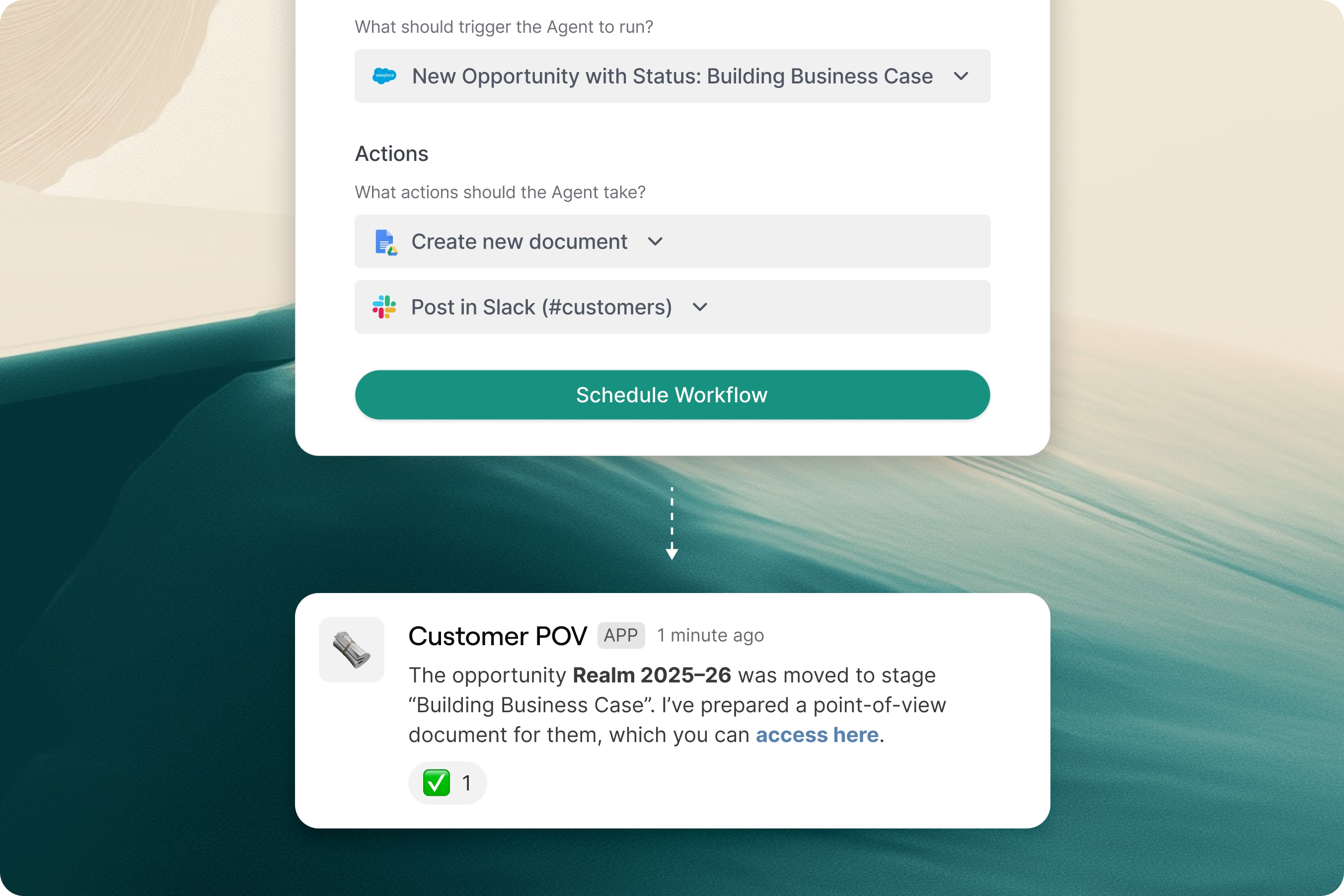
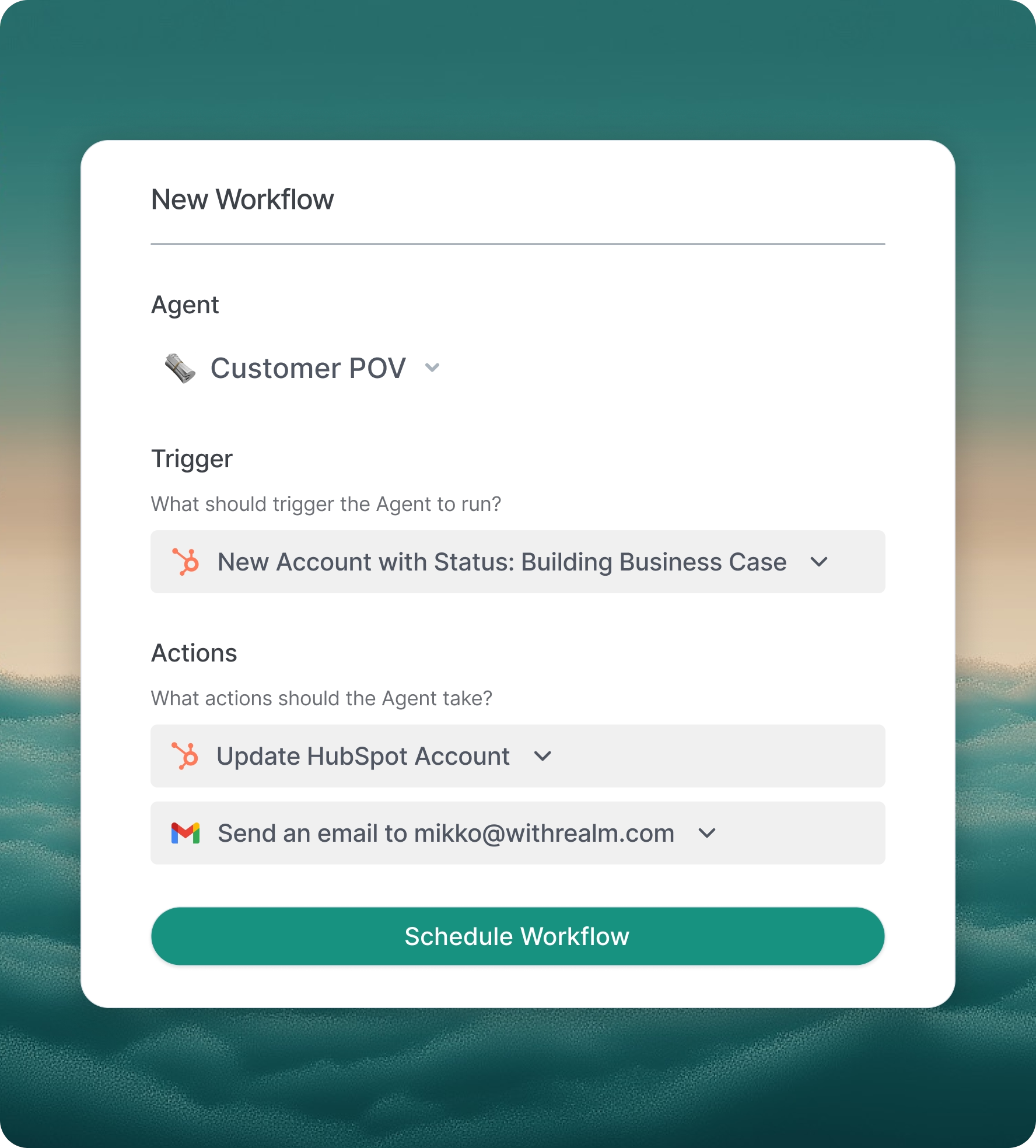
Automate with triggers and actions
Trigger agents to take action in external systems based on events and schedules. Manage your agent workforce on one platform.
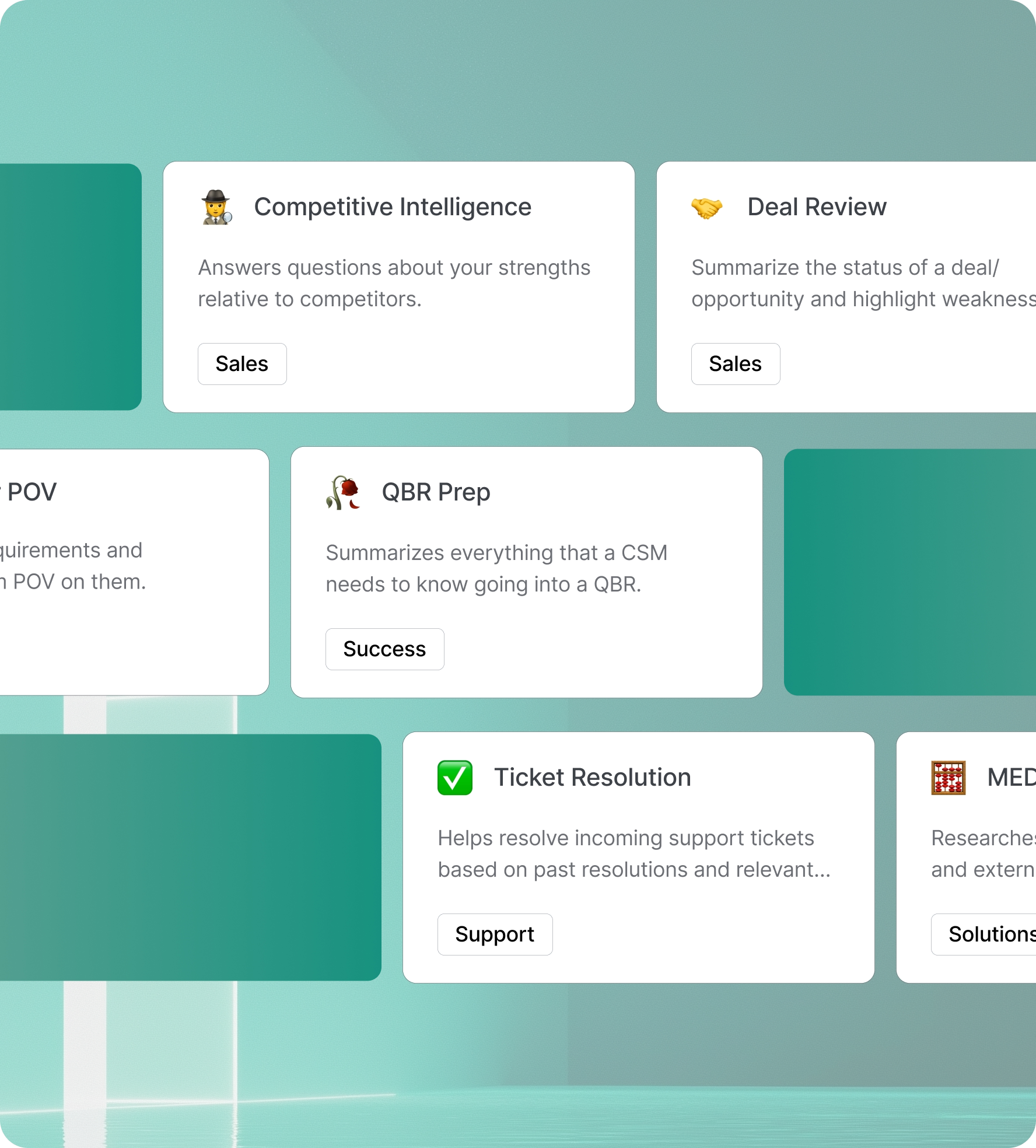
Get started with pre-built templates
Choose from pre-built agent templates for sales, solutions, customer success and support. Share your own templates with your team.

Frends improves sales efficiency with Realm
Automate your work with Realm Agents
Turn knowledge into execution with AI agents
Frequently asked questions about Realm Agents
What are Realm Agents?
Realm Agents are advanced AI tools designed to help revenue teams automate their workflows. You can choose from a library of pre-built agent templates for common use cases in presales, sales, customer success, and support, or create your own custom agents without writing any code. Agents are powered by your company’s knowledge, connected tools, and configurable triggers and actions, enabling automation that is accurate, secure, and tailored to your business.
How do the AI agents work?
Realm Agents are built by defining their capabilities, writing clear step-by-step instructions, and connecting them to your company’s knowledge sources such as documents, folders, and applications. You can choose the most suitable Large Language Model from providers like OpenAI, Anthropic, or Google for each task. Agents can also run automatically through triggers and define where outputs are sent. You can get started instantly with pre-built agents for common use cases across sales, solutions, customer success, and support.
How do AI agents differ from chatbots or automation tools?
While traditional automation follows rigid, pre-set rules, AI agents are more dynamic. They can be trained on your specific business context, execute complex multi-step workflows, make decisions, and take actions across the apps your team already uses. They function more like a team member than a simple tool, capable of handling tasks autonomously from start to finish.
Will AI agents replace my sales and support teams?
No. AI agents are designed to augment your team, not replace them. By automating repetitive and time-consuming tasks, agents free up your team members to focus on high-value work that requires a human touch, such as building customer relationships, strategic thinking, and winning deals.
What can I use the AI agents for?
Realm offers pre-built AI agents for high-impact workflows across sales, presales, customer success, and support. Common use cases include preparing for QBRs, completing MEDDPICC analysis, creating customer POV documents, reviewing deals, calculating customer health scores, and resolving support tickets. You can also build custom agents for tasks such as automating responses to security questionnaires, preparing customer meeting summaries, or gathering competitive intelligence.
Can I build my own AI agents with Realm?
Yes. Realm allows you to build tailored AI agents without writing a single line of code. You can define each agent’s purpose, write its instructions, specify the knowledge it can access, and connect it to your existing systems. Agents can also use tools, triggers, and actions to automate workflows end to end, making them powerful extensions of your team.
What knowledge sources can I train my AI agents on?
You can train your agents by selecting the specific applications, folders, and documents they can access. This ensures each agent operates within your company’s business context and delivers accurate, relevant responses. Realm supports more than 25 native connectors to popular business tools, making it easy to bring all your knowledge together.
Can the AI agents work autonomously?
Yes. You can automate your AI workforce by setting up triggers that assign work to agents automatically. The platform enables you to manage these triggers, allocate tasks to different agents, and take action across external systems.
What AI models do the AI agents use?
Realm gives you the flexibility to choose from the latest and most capable LLMs for your agents, including models from OpenAI, Anthropic, and Google. This enables you to select the most suitable model for each specific task.
How do you ensure the security and privacy of my data?
Realm has been built with security and privacy in mind since day one. AI agents are trained only on the specific knowledge sources you provide, ensuring they operate within a controlled environment. Integrating with your existing systems is done securely, mirroring existing user permissions. You can find more information about our approach to security and privacy here.
How do the agents integrate with my existing applications, such as my CRM?
Realm integrates directly with your existing applications through native connectors and secure APIs. This allows agents to access information, update records, and take action within tools like your CRM, help desk, or documentation platforms. You can define workflows and triggers that let agents work seamlessly across your tech stack as part of a unified AI workforce.
What is the main benefit of using AI agents?
AI agents let your teams focus on what matters most: your customers. They take care of routine, repetitive work like RFPs and internal questions, so your team can spend more time on strategic deals, customer conversations, and creative problem-solving. With agents handling the busywork, your organization can accomplish more with fewer resources.
How do I get started with AI agents for my team?
Getting started with AI agents is simple. You can choose from Realm’s library of pre-built agents designed for common revenue team workflows to see an immediate impact. From there, identify high-effort or repetitive processes in your organization and build custom agents to automate them. Schedule a demo, and we’ll show you exactly how Realm can work for your use cases.
How difficult is it to set up Realm Agents?
Realm is designed for seamless implementation, allowing us to get you up and running in under 24 hours. Get in touch with us to get started today.
How does pricing work for the AI agents?
All Realm plans come with unlimited use of AI agents, including both pre-built agent templates and custom agents you can build with our intuitive AI agent without writing any code. You can find more information about our pricing plans here.
How can I measure the ROI of implementing AI agents?
ROI of AI agents can be measured through several key metrics, including:
- Time saved: Reduction in hours spent on manual tasks like searching for information or filling out questionnaires.
- Increased efficiency: Faster response times to customer inquiries and accelerated sales cycles.
- Improved accuracy: Reduction in errors from manual data entry or inconsistent information.
- Team productivity: Enabling team members to handle a higher volume of high-value work with the same headcount.